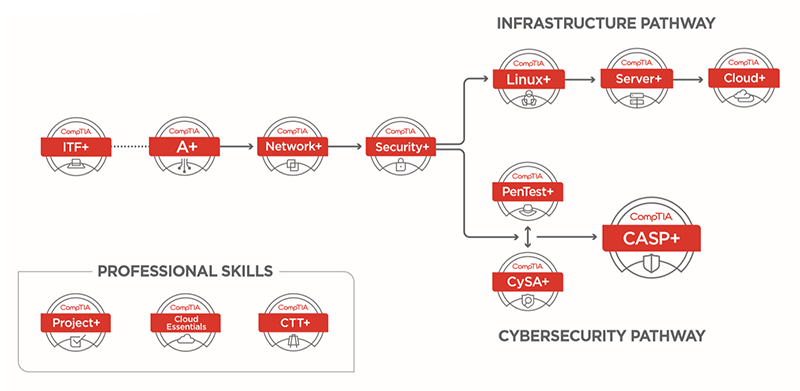
The CompTIA Cybersecurity Analyst (CySA+) course provides essential skills for detecting and mitigating cybersecurity threats through advanced incident response and vulnerability management. Participants will gain expertise in system hardening, analyzing network indicators of compromise, and managing tools like SIEM, SOAR, and endpoint detection. This course emphasizes threat intelligence, secure coding practices, and incident reporting, preparing learners for real-world challenges. Through hands-on labs, students will master techniques for security automation, intrusion analysis, and compliance reporting. The CySA+ certification validates critical skills needed for proactive defense, making it ideal for security analysts, threat hunters, and IT professionals seeking to enhance their cybersecurity capabilities with comprehensive CompTIA CySA+ training.
These skills demonstrate your ability to detect threats, respond to incidents, and maintain proactive cybersecurity measures effectively.

Purchase This Course
USD
View Fees Breakdown
| Course Fee | 2,400 |
|
Total Fees (without exam) |
2,400 (USD) |
♱ Excluding VAT/GST
You can request classroom training in any city on any date by Requesting More Information
♱ Excluding VAT/GST
You can request classroom training in any city on any date by Requesting More Information
1. Certified SOC Analyst v1 (CSA) CompTIA Cybersecurity Analyst (CySA+) and Certified SOC Analyst (CSA) are courses focused on cybersecurity and security operations center (SOC) analysis Read More
To ensure that participants can fully benefit from the CompTIA Cybersecurity Analyst (CySA+) course and have a positive learning experience, the following prerequisites are recommended:
While these prerequisites are not mandatory, they are highly recommended to ensure a successful learning experience in the CompTIA Cybersecurity Analyst (CySA+) course.
| Exam Component | Details |
|---|---|
| Exam Name | CompTIA Cybersecurity Analyst (CySA+) |
| Exam Type | Multiple Choice Questions (MCQs) and Performance-Based Questions (PBQs) |
| Total Questions | 85 (Maximum) |
| Passing Score | 750 (out of 900) |
| Exam Duration | 165 minutes |
| Language | English, Japanese, and other languages as available |
| Exam Provider | CompTIA |
| Exam Registration | Through Pearson VUE's official testing centers or online proctoring |
| Certification Validity | 3 years (can be renewed through Continuing Education Program) |
| Recommended Training | CompTIA CySA+ Training Course |
The CompTIA CySA+ course provides in-depth knowledge of threat detection, incident response, and vulnerability management. Participants will master security operations, threat intelligence, and the application of security tools and frameworks.
Learning Objectives and Outcomes:
Security Operations
Explain the importance of system and network architecture concepts in security operations.
• Log ingestion
- Time synchronization
- Logging levels
• Operating system (OS) concepts
- Windows Registry
- System hardening
- File structure
o Configuration file locations
- System processes
- Hardware architecture
• Infrastructure concepts
- Serverless
- Virtualization
• Network architecture
- On-premises
- Cloud
- Hybrid
- Network segmentation
- Zero trust
- Secure access secure edge (SASE)
- Software-defined networking (SDN)
• Identity and access management
- Multifactor authentication (MFA)
- Single sign-on (SSO)
- Federation
- Privileged access management (PAM)
- Passwordless
- Cloud access security broker (CASB)
• Encryption
- Public key infrastructure (PKI)
- Secure sockets layer (SSL) inspection
• Sensitive data protection
- Data loss prevention (DLP)
- Personally identifiable information (PII)
- Cardholder data (CHD)
Given a scenario, analyze indicators of potentially malicious activity.
• Network-related
- Bandwidth consumption
- Beaconing
- Irregular peer-to-peer communication
- Rogue devices on the network
- Scans/sweeps
- Unusual traffic spikes
- Activity on unexpected ports
• Host-related
- Processor consumption
- Memory consumption
- Drive capacity consumption
- Unauthorized software
- Malicious processes
- Unauthorized changes
- Unauthorized privileges
- Data exfiltration
- Abnormal OS process behavior
- File system changes or anomalies
- Registry changes or anomalies
- Unauthorized scheduled tasks
• Application-related
- Anomalous activity
- Introduction of new accounts
- Unexpected output
- Unexpected outbound communication
- Service interruption
- Application logs
• Other
- Social engineering attacks
- Obfuscated links
Given a scenario, use appropriate tools or techniques to determine malicious activity.
• Tools
- Packet capture
o Wireshark
o tcpdump
- Log analysis/correlation
o Security information and event management (SIEM)
o Security orchestration, automation, and response (SOAR)
- Endpoint security
o Endpoint detection and response (EDR)
- Domain name service (DNS) and Internet Protocol (IP) reputation
o WHOIS
o AbuseIPDB
- File analysis
o Strings
o VirusTotal
- Sandboxing
o Joe Sandbox
o Cuckoo Sandbox
• Common techniques
- Pattern recognition
o Command and control
- Interpreting suspicious commands
- Email analysis
o Header
o Impersonation
o DomainKeys Identified Mail (DKIM)
o Domain-based Message Authentication, Reporting, and Conformance (DMARC)
o Sender Policy Framework (SPF)
o Embedded links
- File analysis
o Hashing
- User behavior analysis
o Abnormal account activity
o Impossible travel
• Programming languages/scripting
- JavaScript Object Notation (JSON)
- Extensible Markup Language (XML)
- Python
- PowerShell
- Shell script
- Regular expressions
Compare and contrast threat-intelligence and threat-hunting concepts.
• Threat actors
- Advanced persistent threat (APT)
- Hacktivists
- Organized crime
- Nation-state
- Script kiddie
- Insider threat
o Intentional
o Unintentional
- Supply chain
• Tactics, techniques, and procedures (TTP)
• Confidence levels
- Timeliness
- Relevancy
- Accuracy
• Collection methods and sources
- Open source
o Social media
o Blogs/forums
o Government bulletins
o Computer emergency response team (CERT)
o Cybersecurity incident response team (CSIRT)
o Deep/dark web
- Closed source
o Paid feeds
o Information sharing organizations
o Internal sources
• Threat intelligence sharing
- Incident response
- Vulnerability management
- Risk management
- Security engineering
- Detection and monitoring
• Threat hunting
- Indicators of compromise (IoC)
o Collection
o Analysis
o Application
- Focus areas
o Configurations/ misconfigurations
o Isolated networks
o Business-critical assets and processes
- Active defense
- Honeypot
Explain the importance of efficiency and process improvement in security operations.
• Standardize processes
- Identification of tasks suitable for automation
o Repeatable/do not require human interaction
- Team coordination to manage and facilitate automation
• Streamline operations
- Automation and orchestration
o Security orchestration, automation, and response (SOAR)
- Orchestrating threat intelligence data
o Data enrichment
o Threat feed combination
- Minimize human engagement
• Technology and tool integration
- Application programming interface (API)
- Webhooks
- Plugins
• Single pane of glass
2.0 Vulnerability Management
Given a scenario, implement vulnerability scanning methods and concepts.
• Asset discovery
- Map scans
- Device fingerprinting
• Special considerations
- Scheduling
- Operations
- Performance
- Sensitivity levels
- Segmentation
- Regulatory requirements
• Internal vs. external scanning
• Agent vs. agentless
• Credentialed vs. non-credentialed
• Passive vs. active
• Static vs. dynamic
- Reverse engineering
- Fuzzing
• Critical infrastructure
- Operational technology (OT)
- Industrial control systems (ICS)
- Supervisory control and data acquisition (SCADA)
• Security baseline scanning
• Industry frameworks
- Payment Card Industry Data Security Standard (PCI DSS)
- Center for Internet Security (CIS) benchmarks
- Open Web Application Security Project (OWASP)
- International Organization for Standardization (ISO) 27000 series
Given a scenario, analyze output from vulnerability assessment tools.
• Tools
- Network scanning and mapping
o Angry IP Scanner
o Maltego
- Web application scanners
o Burp Suite
o Zed Attack Proxy (ZAP)
o Arachni
o Nikto
- Vulnerability scanners
o Nessus
o OpenVAS
- Debuggers
o Immunity debugger
o GNU debugger (GDB)
- Multipurpose
o Nmap
o Metasploit framework (MSF)
o Recon-ng
- Cloud infrastructure assessment tools
o Scout Suite
o Prowler
o Pacu
Given a scenario, analyze data to prioritize vulnerabilities.
• Common Vulnerability Scoring System (CVSS) interpretation
- Attack vectors
- Attack complexity
- Privileges required
- User interaction
- Scope
- Impact
o Confidentiality
o Integrity
o Availability
• Validation
- True/false positives
- True/false negatives
• Context awareness
- Internal
- External
- Isolated
• Exploitability/weaponization
• Asset value
• Zero-day
Given a scenario, recommend controls to mitigate attacks and software vulnerabilities.
• Cross-site scripting
- Reflected
- Persistent
• Overflow vulnerabilities
- Buffer
- Integer
- Heap
- Stack
• Data poisoning
• Broken access control
• Cryptographic failures
• Injection flaws
• Cross-site request forgery
• Directory traversal
• Insecure design
• Security misconfiguration
• End-of-life or outdated components
• Identification and authentication failures
• Server-side request forgery
• Remote code execution
• Privilege escalation
• Local file inclusion (LFI)/remote file inclusion (RFI)
Explain concepts related to vulnerability response, handling, and management.
• Compensating control
• Control types
- Managerial
- Operational
- Technical
- Preventative
- Detective
- Responsive
- Corrective
• Patching and configuration management
- Testing
- Implementation
- Rollback
- Validation
• Maintenance windows
• Exceptions
• Risk management principles
- Accept
- Transfer
- Avoid
- Mitigate
• Policies, governance, and servicelevel objectives (SLOs)
• Prioritization and escalation
• Attack surface management
- Edge discovery
- Passive discovery
- Security controls testing
- Penetration testing and adversary emulation
- Bug bounty
- Attack surface reduction
• Secure coding best practices
- Input validation
- Output encoding
- Session management
- Authentication
- Data protection
- Parameterized queries
• Secure software development life cycle (SDLC)
• Threat modelling
Incident Response and Management
Explain concepts related to attack methodology frameworks.
• Cyber kill chains
• Diamond Model of Intrusion Analysis
• MITRE ATT&CK
• Open Source Security Testing Methodology Manual (OSS TMM)
Given a scenario, perform incident response activities.
• Detection and analysis
- IoC
- Evidence acquisitions
o Chain of custody
o Validating data integrity
o Preservation
o Legal hold
- Data and log analysis
• Containment, eradication, and recovery
- Scope
- Impact
- Isolation
- Remediation
- Re-imaging
- Compensating controls
Explain the preparation and post-incident activity phases of the incident management life cycle.
• Preparation
- Incident response plan
- Tools
- Playbooks
- Tabletop
- Training
- Business continuity (BC)/disaster recovery (DR)
• Post-incident activity
- Forensic analysis
- Root cause analysis
- Lessons learned
Reporting and Communication
Explain the importance of vulnerability management reporting and communication.
• Vulnerability management reporting
- Vulnerabilities
- Affected hosts
- Risk score
- Mitigation
- Recurrence
- Prioritization
• Compliance reports
• Action plans
- Configuration management
- Patching
- Compensating controls
- Awareness, education, and training
- Changing business requirements
• Inhibitors to remediation
- Memorandum of understanding (MOU)
- Service-level agreement (SLA)
- Organizational governance
- Business process interruption
- Degrading functionality
- Legacy systems
- Proprietary systems
• Metrics and key performance indicators (KPIs)
- Trends
- Top 10
- Critical vulnerabilities and zero-days
- SLOs
• Stakeholder identification and communication
Explain the importance of incident response reporting and communication.
• Stakeholder identification and communication
• Incident declaration and escalation
• Incident response reporting
- Executive summary
- Who, what, when, where, and why
- Recommendations
- Timeline
- Impact
- Scope
- Evidence
• Communications
- Legal
- Public relations
o Customer communication
o Media
- Regulatory reporting
- Law enforcement
• Root cause analysis
• Lessons learned
• Metrics and KPIs
- Mean time to detect
- Mean time to respond
- Mean time to remediate
- Alert volume
Threat management in cybersecurity involves identifying, assessing, and mitigating risks to digital infrastructure and data. It is a critical practice that ensures systems remain safe from unauthorized access, attacks, and other security breaches. Professionals pursuing threat management can benefit from obtaining a CompTIA CySA+ certification (Cybersecurity Analyst). This certification equips analysts with the necessary skills to effectively monitor and respond to security threats, thus improving an organization's security posture. The CySA+ training helps in mastering techniques for managing and countering threats, emphasizing the importance of proactive security measures.
Forensic tools in cybersecurity are software applications used to collect, preserve, analyze, and present digital evidence from computers and other devices. These tools help professionals identify how a security breach occurred, recover lost data, and understand malicious activities. They are crucial for investigations in data breaches, cybercrimes and ensuring compliance with regulations. Effective use of forensic tools requires specialized knowledge, often covered in Cybersecurity Analyst Training such as the CompTIA CySA+ certification, which prepares analysts to use these tools proficiently in both identifying and mitigating security vulnerabilities.
Vulnerability management is a cybersecurity process to systematically identify, categorize, prioritize, and address security weaknesses in an organization’s IT environment. This practice is crucial for protecting sensitive data and systems from attacks. It involves regular scanning and analysis to detect vulnerabilities, followed by deploying appropriate measures such as patches or fixes to mitigate risks. Effective vulnerability management reduces the attack surface, making it harder for attackers to exploit systems, thus enhancing overall security posture. Cybersecurity Analyst Training, including programs like CompTIA CySA+, equips professionals with the skills necessary for effective vulnerability management.
Security architecture is a structured framework that defines how security measures and controls are positioned within a network to protect an organization's information technology (IT) systems and data. This architecture includes identifying potential threats, designing the network's security layout, and implementing security policies and procedures to manage risks effectively. It helps organizations anticipate and mitigate security breaches by setting up layered defense mechanisms. The concept is vital in creating a secure environment for data and applications, ensuring that only authorized users have access and preventing unauthorized access, data breaches, and other cybersecurity threats.
Frameworks in technology refer to structured platforms used to develop applications and systems. They provide predefined functionalities and foundations, allowing developers to build software efficiently and maintain it effectively. Frameworks handle common programming tasks and help manage software complexity by offering a systematic way to build and deploy applications. They typically incorporate libraries, APIs, and tools configured to work together seamlessly, simplifying the development process and enabling code reuse. Frameworks are critical in numerous technological areas, including web development, mobile application development, and computer security. Examples are .NET for Windows applications and React for interactive websites.
Risk evaluation in cybersecurity involves assessing the potential threats and vulnerabilities to an organization's information systems and data. It identifies the risks of unauthorized access, data breaches, and system disruptions. By evaluating these risks, organizations can prioritize and apply appropriate security measures to mitigate these threats. This is crucial in safeguarding sensitive information and maintaining system integrity.
Penetration testing is a method used to test a computer system, network, or web application to find vulnerabilities that an attacker could exploit. In essence, it simulates an attack on a system to check for security weaknesses. Penetration testers use various techniques and tools to assess the security of an IT infrastructure. By identifying and addressing vulnerabilities, organizations can significantly reduce their risk profile. CySA (Cybersecurity Analyst) and CompTIA CySA+ certification courses are professional training pathways that focus on the necessary skills for cybersecurity analysts, including penetration testing.
Incident response is a predetermined approach to addressing and managing the aftermath of a security breach or cyberattack, also known as an IT incident, computer incident, or security incident. The goal is to handle the situation in a way that limits damage and reduces recovery time and costs. An effective incident response plan involves a series of steps that the response team follows during an incident. These steps typically include identification, containment, eradication, recovery, and lessons learned. Cybersecurity Analyst Training, like the CompTIA CySA+ certification, prepares professionals to effectively manage and neutralize security incidents in real-world situations.
The CompTIA CySA+ course provides in-depth knowledge of threat detection, incident response, and vulnerability management. Participants will master security operations, threat intelligence, and the application of security tools and frameworks.
Learning Objectives and Outcomes:
Security Operations
Explain the importance of system and network architecture concepts in security operations.
• Log ingestion
- Time synchronization
- Logging levels
• Operating system (OS) concepts
- Windows Registry
- System hardening
- File structure
o Configuration file locations
- System processes
- Hardware architecture
• Infrastructure concepts
- Serverless
- Virtualization
• Network architecture
- On-premises
- Cloud
- Hybrid
- Network segmentation
- Zero trust
- Secure access secure edge (SASE)
- Software-defined networking (SDN)
• Identity and access management
- Multifactor authentication (MFA)
- Single sign-on (SSO)
- Federation
- Privileged access management (PAM)
- Passwordless
- Cloud access security broker (CASB)
• Encryption
- Public key infrastructure (PKI)
- Secure sockets layer (SSL) inspection
• Sensitive data protection
- Data loss prevention (DLP)
- Personally identifiable information (PII)
- Cardholder data (CHD)
Given a scenario, analyze indicators of potentially malicious activity.
• Network-related
- Bandwidth consumption
- Beaconing
- Irregular peer-to-peer communication
- Rogue devices on the network
- Scans/sweeps
- Unusual traffic spikes
- Activity on unexpected ports
• Host-related
- Processor consumption
- Memory consumption
- Drive capacity consumption
- Unauthorized software
- Malicious processes
- Unauthorized changes
- Unauthorized privileges
- Data exfiltration
- Abnormal OS process behavior
- File system changes or anomalies
- Registry changes or anomalies
- Unauthorized scheduled tasks
• Application-related
- Anomalous activity
- Introduction of new accounts
- Unexpected output
- Unexpected outbound communication
- Service interruption
- Application logs
• Other
- Social engineering attacks
- Obfuscated links
Given a scenario, use appropriate tools or techniques to determine malicious activity.
• Tools
- Packet capture
o Wireshark
o tcpdump
- Log analysis/correlation
o Security information and event management (SIEM)
o Security orchestration, automation, and response (SOAR)
- Endpoint security
o Endpoint detection and response (EDR)
- Domain name service (DNS) and Internet Protocol (IP) reputation
o WHOIS
o AbuseIPDB
- File analysis
o Strings
o VirusTotal
- Sandboxing
o Joe Sandbox
o Cuckoo Sandbox
• Common techniques
- Pattern recognition
o Command and control
- Interpreting suspicious commands
- Email analysis
o Header
o Impersonation
o DomainKeys Identified Mail (DKIM)
o Domain-based Message Authentication, Reporting, and Conformance (DMARC)
o Sender Policy Framework (SPF)
o Embedded links
- File analysis
o Hashing
- User behavior analysis
o Abnormal account activity
o Impossible travel
• Programming languages/scripting
- JavaScript Object Notation (JSON)
- Extensible Markup Language (XML)
- Python
- PowerShell
- Shell script
- Regular expressions
Compare and contrast threat-intelligence and threat-hunting concepts.
• Threat actors
- Advanced persistent threat (APT)
- Hacktivists
- Organized crime
- Nation-state
- Script kiddie
- Insider threat
o Intentional
o Unintentional
- Supply chain
• Tactics, techniques, and procedures (TTP)
• Confidence levels
- Timeliness
- Relevancy
- Accuracy
• Collection methods and sources
- Open source
o Social media
o Blogs/forums
o Government bulletins
o Computer emergency response team (CERT)
o Cybersecurity incident response team (CSIRT)
o Deep/dark web
- Closed source
o Paid feeds
o Information sharing organizations
o Internal sources
• Threat intelligence sharing
- Incident response
- Vulnerability management
- Risk management
- Security engineering
- Detection and monitoring
• Threat hunting
- Indicators of compromise (IoC)
o Collection
o Analysis
o Application
- Focus areas
o Configurations/ misconfigurations
o Isolated networks
o Business-critical assets and processes
- Active defense
- Honeypot
Explain the importance of efficiency and process improvement in security operations.
• Standardize processes
- Identification of tasks suitable for automation
o Repeatable/do not require human interaction
- Team coordination to manage and facilitate automation
• Streamline operations
- Automation and orchestration
o Security orchestration, automation, and response (SOAR)
- Orchestrating threat intelligence data
o Data enrichment
o Threat feed combination
- Minimize human engagement
• Technology and tool integration
- Application programming interface (API)
- Webhooks
- Plugins
• Single pane of glass
2.0 Vulnerability Management
Given a scenario, implement vulnerability scanning methods and concepts.
• Asset discovery
- Map scans
- Device fingerprinting
• Special considerations
- Scheduling
- Operations
- Performance
- Sensitivity levels
- Segmentation
- Regulatory requirements
• Internal vs. external scanning
• Agent vs. agentless
• Credentialed vs. non-credentialed
• Passive vs. active
• Static vs. dynamic
- Reverse engineering
- Fuzzing
• Critical infrastructure
- Operational technology (OT)
- Industrial control systems (ICS)
- Supervisory control and data acquisition (SCADA)
• Security baseline scanning
• Industry frameworks
- Payment Card Industry Data Security Standard (PCI DSS)
- Center for Internet Security (CIS) benchmarks
- Open Web Application Security Project (OWASP)
- International Organization for Standardization (ISO) 27000 series
Given a scenario, analyze output from vulnerability assessment tools.
• Tools
- Network scanning and mapping
o Angry IP Scanner
o Maltego
- Web application scanners
o Burp Suite
o Zed Attack Proxy (ZAP)
o Arachni
o Nikto
- Vulnerability scanners
o Nessus
o OpenVAS
- Debuggers
o Immunity debugger
o GNU debugger (GDB)
- Multipurpose
o Nmap
o Metasploit framework (MSF)
o Recon-ng
- Cloud infrastructure assessment tools
o Scout Suite
o Prowler
o Pacu
Given a scenario, analyze data to prioritize vulnerabilities.
• Common Vulnerability Scoring System (CVSS) interpretation
- Attack vectors
- Attack complexity
- Privileges required
- User interaction
- Scope
- Impact
o Confidentiality
o Integrity
o Availability
• Validation
- True/false positives
- True/false negatives
• Context awareness
- Internal
- External
- Isolated
• Exploitability/weaponization
• Asset value
• Zero-day
Given a scenario, recommend controls to mitigate attacks and software vulnerabilities.
• Cross-site scripting
- Reflected
- Persistent
• Overflow vulnerabilities
- Buffer
- Integer
- Heap
- Stack
• Data poisoning
• Broken access control
• Cryptographic failures
• Injection flaws
• Cross-site request forgery
• Directory traversal
• Insecure design
• Security misconfiguration
• End-of-life or outdated components
• Identification and authentication failures
• Server-side request forgery
• Remote code execution
• Privilege escalation
• Local file inclusion (LFI)/remote file inclusion (RFI)
Explain concepts related to vulnerability response, handling, and management.
• Compensating control
• Control types
- Managerial
- Operational
- Technical
- Preventative
- Detective
- Responsive
- Corrective
• Patching and configuration management
- Testing
- Implementation
- Rollback
- Validation
• Maintenance windows
• Exceptions
• Risk management principles
- Accept
- Transfer
- Avoid
- Mitigate
• Policies, governance, and servicelevel objectives (SLOs)
• Prioritization and escalation
• Attack surface management
- Edge discovery
- Passive discovery
- Security controls testing
- Penetration testing and adversary emulation
- Bug bounty
- Attack surface reduction
• Secure coding best practices
- Input validation
- Output encoding
- Session management
- Authentication
- Data protection
- Parameterized queries
• Secure software development life cycle (SDLC)
• Threat modelling
Incident Response and Management
Explain concepts related to attack methodology frameworks.
• Cyber kill chains
• Diamond Model of Intrusion Analysis
• MITRE ATT&CK
• Open Source Security Testing Methodology Manual (OSS TMM)
Given a scenario, perform incident response activities.
• Detection and analysis
- IoC
- Evidence acquisitions
o Chain of custody
o Validating data integrity
o Preservation
o Legal hold
- Data and log analysis
• Containment, eradication, and recovery
- Scope
- Impact
- Isolation
- Remediation
- Re-imaging
- Compensating controls
Explain the preparation and post-incident activity phases of the incident management life cycle.
• Preparation
- Incident response plan
- Tools
- Playbooks
- Tabletop
- Training
- Business continuity (BC)/disaster recovery (DR)
• Post-incident activity
- Forensic analysis
- Root cause analysis
- Lessons learned
Reporting and Communication
Explain the importance of vulnerability management reporting and communication.
• Vulnerability management reporting
- Vulnerabilities
- Affected hosts
- Risk score
- Mitigation
- Recurrence
- Prioritization
• Compliance reports
• Action plans
- Configuration management
- Patching
- Compensating controls
- Awareness, education, and training
- Changing business requirements
• Inhibitors to remediation
- Memorandum of understanding (MOU)
- Service-level agreement (SLA)
- Organizational governance
- Business process interruption
- Degrading functionality
- Legacy systems
- Proprietary systems
• Metrics and key performance indicators (KPIs)
- Trends
- Top 10
- Critical vulnerabilities and zero-days
- SLOs
• Stakeholder identification and communication
Explain the importance of incident response reporting and communication.
• Stakeholder identification and communication
• Incident declaration and escalation
• Incident response reporting
- Executive summary
- Who, what, when, where, and why
- Recommendations
- Timeline
- Impact
- Scope
- Evidence
• Communications
- Legal
- Public relations
o Customer communication
o Media
- Regulatory reporting
- Law enforcement
• Root cause analysis
• Lessons learned
• Metrics and KPIs
- Mean time to detect
- Mean time to respond
- Mean time to remediate
- Alert volume