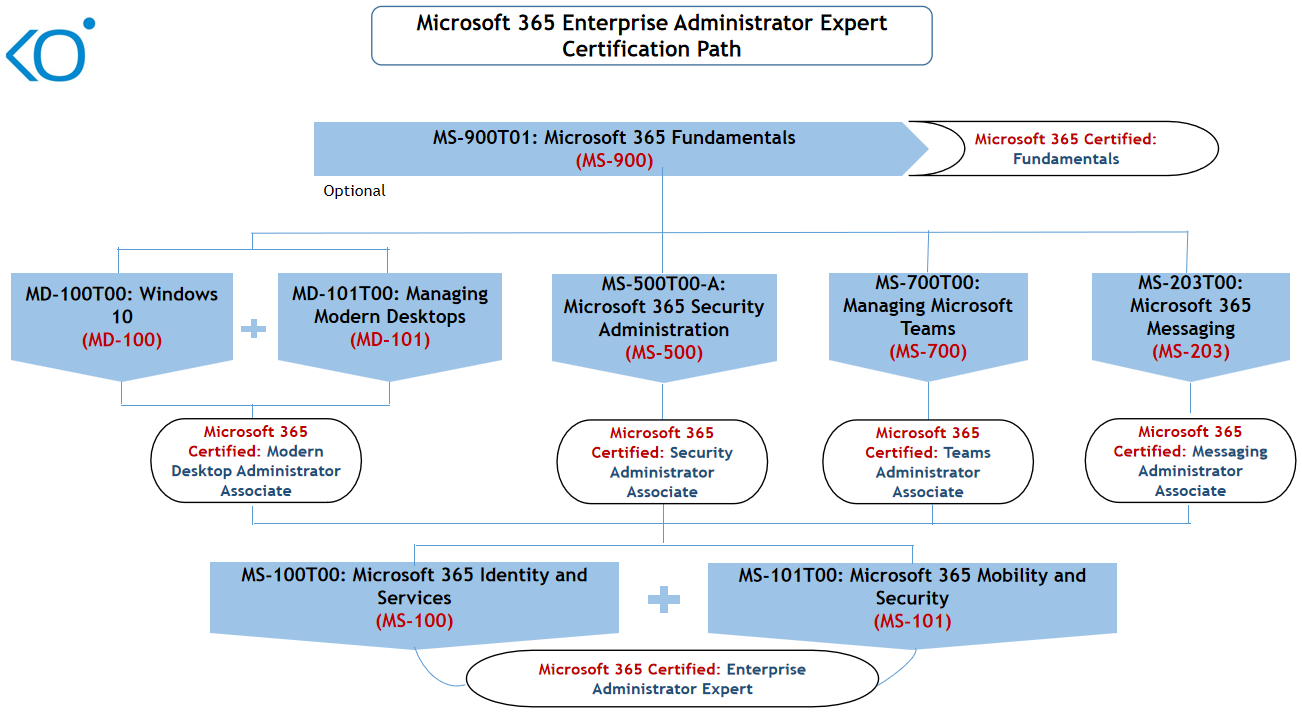
The MS-101: Microsoft 365 Mobility and Security course is designed to equip learners with the knowledge and skills required to implement, manage, and monitor security and compliance solutions for Microsoft 365 and hybrid environments. The course covers key aspects of Microsoft 365 security management, including Threat protection, Security governance, data governance, and Device management.
By delving into Microsoft 101 training, participants will gain insights into Threat vectors, Data breaches, advanced Threat protection, data governance, and mobile Device management strategies. The course structure includes hands-on labs and practical lessons, providing a comprehensive understanding of the Zero Trust Model, Microsoft Secure Score, Privileged Identity Management, and Azure Active Directory Identity Protection.
Learners will benefit from understanding Microsoft office 101, as it enables them to enhance their organization's security posture, implement Threat intelligence, Data loss prevention, and ensures compliance with legal and regulatory standards. This course is vital for IT professionals looking to advance their career in Microsoft 365 security administration.

Purchase This Course
USD
View Fees Breakdown
| Course Fee | 2,500 |
|
Total Fees |
2,500 (USD) |
♱ Excluding VAT/GST
You can request classroom training in any city on any date by Requesting More Information
♱ Excluding VAT/GST
You can request classroom training in any city on any date by Requesting More Information


To ensure you are well-prepared for the MS-101: Microsoft 365 Mobility and Security course, the following prerequisites are recommended:
While these are the minimum required knowledge areas, the course is designed to be accessible to individuals who have foundational IT skills and a keen interest to learn about Microsoft 365 Mobility and Security. Being proactive in your learning will help overcome any knowledge gaps during the course.
The MS-101 course equips IT professionals with skills to secure Microsoft 365 enterprise environments.
Target Audience:
Gain critical skills in Microsoft 365 security management, including threat protection, security governance, and data compliance with the MS-101 course.
Security governance involves managing and overseeing an organization's security policies, strategies, and procedures to protect its information and technology assets. This includes developing clear security protocols, ensuring they are followed, and assessing their effectiveness. It plays a critical role in maintaining compliance with laws and regulations and helps in managing risks associated with data breaches and cyber threats. Effective security governance requires collaboration across all levels of an organization and integrates principles and tools, such as those found in Microsoft 365 mobility and security, to safeguard data and resources comprehensively.
Data governance is the management framework that ensures data is accurate, available, and secure within an organization. This framework involves policies, procedures, and technologies to manage data assets effectively. It promotes data quality, helps maintain consistency, and drives compliance with data-related regulations. Data governance enables organizations to extract more value from their data, make better decisions, and support business objectives. Proper governance is crucial for data-driven environments, especially those leveraging advanced technologies like Microsoft 365 mobility and security tools, ensuring that data used across platforms remains well managed and protected.
Device management is a process used to oversee, manage, and secure employees' mobile devices and computers within an organization. Utilizing platforms like Microsoft 365 Mobility and Security, businesses can control access to internal data, enforce security policies, and ensure all devices comply with corporate standards. This management is crucial in a modern workspace where employees may use multiple devices to access sensitive company resources both in-office and remotely. Microsoft 365 Mobility and Security training empowers IT professionals by equipping them with knowledge and skills to execute efficient device management across the enterprise.
Threat vectors are methods or pathways that malicious actors use to infiltrate and harm digital systems, networks, or data. Common threat vectors include malware, phishing, and hacking. In the context of Microsoft 365 Mobility and Security, these vectors become particularly relevant as they can compromise remote access, data integrity, and user identity. Effective training in Microsoft 365 Mobility and Security helps users understand and mitigate potential threats, enhancing overall system protection by leveraging advanced security features and best practices specific to Microsoft environments.
Advanced threat protection (ATP) is a security solution that helps defend against sophisticated cyber threats such as malware, ransomware, and phishing attacks. It is commonly integrated into platforms like Microsoft 365, enhancing mobility and security by continuously monitoring and analyzing threat data to provide real-time protection. ATP leverages machine learning and behavioral analytics to detect anomalies and respond to breaches swiftly, thereby securing organizational data across various devices and applications. It aims to reduce the risk of advanced cyberattacks, ensuring both safety and compliance within the digital workspace.
Mobile device management (MDM) is a technology used to secure, monitor, and manage the various mobile devices such as smartphones, tablets, and laptops that employees use in the workplace. It helps businesses ensure that these devices comply with company security policies, support necessary applications, and maintain data security. Microsoft 365 mobility and security features enhance MDM by providing tools that integrate seamlessly with other Microsoft products, facilitating better control and security across all devices. This setup is particularly covered in Microsoft 365 mobility and security training, which prepares IT professionals to effectively use and manage these technologies.
The Zero Trust Model is a security framework that requires all users, whether inside or outside the organization’s network, to be authenticated, authorized, and continuously validated before being granted or keeping access to data and applications. It operates on the principle "never trust, always verify," making it an effective approach against data breaches and cyberattacks. This model emphasizes the need for strict access controls and real-time security, significantly reducing the risk of unauthorized access and data exposure.
Azure Active Directory Identity Protection is a feature within Microsoft 365 that safeguards user identities from cybersecurity threats. It monitors and analyzes user actions and sign-in data to detect suspicious activities that might indicate risks. In case of anomalies or outside of typical user behavior patterns, the system can enforce automatic responses, such as requiring additional authentication steps or blocking access altogether. This tool effectively prevents identity theft and unauthorized access, promoting a secure and resilient environment for organizations managing their operations digitally.
Threat intelligence is the collection and analysis of information about potential security threats to help organizations understand, predict, and mitigate cyber risks. This involves studying trends and tactics of cyber attackers, including the technologies and methods they use. By analyzing this data, businesses enhance their security measures, stay ahead of potential threats, and respond more effectively to incidents, thus improving their cybersecurity posture. Proper threat intelligence allows for proactive management of these risks rather than reactive responses, ensuring a higher level of protection for a company’s systems and data.
Microsoft Secure Score is a measurement tool within Microsoft 365 that helps organizations assess and enhance their security posture. By evaluating security configurations, user behaviors, and other security-related activities across Microsoft 365 environments, it offers insights and recommendations. This tool helps in identifying vulnerabilities and suggests actions to mitigate risks, ultimately boosting the overall security of systems. It is integral for professionals managing Microsoft 365 mobility and security, ensuring that security protocols align with best practices to protect sensitive data and infrastructure from potential threats.
Privileged Identity Management (PIM) is a security strategy designed to control, manage, and monitor access to critical resources within an organization. The goal is to ensure that only authorized individuals have access to sensitive systems and data, typically through the use of specialized software. PIM helps prevent security breaches by minimizing the number of people who can access privileged accounts and by tracking their actions when using these accounts. It's a crucial part of maintaining security, particularly for organizations using complex IT environments where the potential impact of mismanaged privileges is significant.
Data loss prevention (DLP) is a strategy and set of tools used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. DLP software monitors, detects, and blocks sensitive data while in use, in motion, and at rest through deep content analysis. It helps in enforcing company policies on data usage and security, and is essential in avoiding data breaches. Microsoft 365 Mobility and Security features DLP capabilities to safeguard business information across all devices and applications while supporting compliance requirements.
A data breach occurs when confidential information is accessed, stolen, or exposed without authorization. This can happen through hacking, accidental disclosure, or inadequate security practices. The consequences can be severe, ranging from identity theft to financial loss for individuals, and reputational damage to businesses. In response, many organizations invest in security measures like Microsoft 365 Mobility and Security training, which helps protect data by managing device and user identities and controlling access to information efficiently. This training is crucial in mitigating the risks associated with data breaches.
Threat protection in Microsoft 365 mobility and security involves safeguarding your data and devices from malicious attacks and unauthorized access. This is essential in maintaining the safety and integrity of your information across various devices and applications. Microsoft 365 mobility and security training equips professionals with the knowledge and skills needed to implement and manage security measures effectively. Tools used in MS 101 or Microsoft 101 trainings empower users to anticipate, address, and neutralize potential security threats, ensuring a secure and reliable environment for business operations and data management.
The MS-101 course equips IT professionals with skills to secure Microsoft 365 enterprise environments.
Target Audience:
Gain critical skills in Microsoft 365 security management, including threat protection, security governance, and data compliance with the MS-101 course.